
December 31, 2009
Dodging, Dazzling, and Divulging

Ruben Pater’s drone identification sheet
The author would like to acknowledge the research of Enya Moore and students of the Design Curating & Writing MA at Design Academy Eindhoven.
++++
We live in an era of algorithmic monitoring in which our purchases, preferences, politics, and perversions are increasingly tagged, tracked, predicted, and sold. The ways in which new media technologies are used by the state and corporations to compile our personal data has emerged as the issue-du-jour of the global design community. Student assignments, thesis projects, conferences, workshops and exhibitions, are busy excavating the substantive implications of living in the post-Snowden age.
While many designers are complicit, even instrumental, in this mass monetization and regulation of our digital identities, others resist, and as a result draw attention to its insidiousness. Some of these instances of resistance are simply informational—meant to help people understand how and why our private and anonymous existence is being eroded, or to incite us take measures to protect it, and to support the work of digital rights activists such as the Tor network, a global network of thousands of volunteer-run servers, relays, and services designed to help anonymize data. Another strategy is to provide tools and tactics to enable more active ways for us to dodge, expose, or fight back against the unwanted attentions of governments and corporations.
The U.S. Federal Aviation Administration (FAA) has recently predicted that by 2020, the skies above America could well be abuzz with up to 7 million commercial, hobbyist and government drones, that’s almost three times as many as we have now. Some of them will be equipped with high definition digital cameras, infrared cameras, and Gorgon Stare sensors. Facial recognition technologies are still in development and are dependent on the compilation of databases of peoples’ faces, but they are already widely being used. High-definition video surveillance, one of the world’s fastest growing industries, accumulates an astonishing 413 petabytes of data a day. In the UK, for example, the British Security Industry Authority (BSIA) has estimated that there are up to 5.9 million CCTV cameras, which equates to one for every eleven citizens, viewing us as many as 300 times a day.
The projects featured below draw attention to the larger topic of surveillance in the physical and digital spaces we inhabit, and aim to enhance understanding of the issue. Most respond to specific technologies—drones, facial recognition software, CCTV, or text scanning software, for example—and provide ways to avoid, jam, or otherwise confuse them. In addition to the informational projects in circulation, are many others that can be considered, according to the primary response that they seek to encourage in their users. There are those that offer us measures through which to retreat and hide ourselves and our data; and those that urge us to confront our surveillants through activist techniques such as “sousveillance” or the pre-emptive exposure of our data, as a challenge to those in power.
DODGING AND DAZZLING
Many of the designed responses to surveillance currently being generated are focused on enabling people to disguise their identities through time-tested camouflage and distraction techniques, such as the creation of extra informational “noise,” updated to evade today’s technologies. This camouflage can be visual, genetic, or digital.
Urban camouflage 
Japanese designer Aya Tsukioka has developed a series of Rube Goldberg-like outfits that enable a very literal form of urban camouflage: a skirt that unfolds into a tent structure printed with the image of a street vending machine, a purse that looks like a manhole cover which you can leave on the street, and a child’s backpack that allows the wearer to disguise themselves as a fire hydrant. Inspired by the ancient ninja, who cloaked themselves in black blankets at night, the items are intended to provide urban dwellers with momentary refuge from attackers or surveillants.

Aya Tsukioka’s mailbox urban camouflage
More recently the Brooklyn-based architecture practice, Snarkitecture issued a series of architectural camouflage garments, intended to create what they call, “moments of architectural confusion, where you become visually lost within different material surfaces.” The initial line uses urban patterns from New York City such as subway station tiles and marble flooring, but since you can upload your own images to the website Print All Over Me, you can create your own urban camouflage customized to your own locale.


Snarkitecture
Similarly, German designers Sabina Keric and Yvonne Bayer made three-dimensional sculptures out of materials including bags of frozen peas or plastic soda bottles in which the wearer merges with retail displays in superstores, as a way to momentarily avoid what they call the “noise of commerce.”

One of Sabina Keric and Yvonne Bayer retail camouflage pieces
Numerous deployments of the principles of the Faraday Cage can also be seen, derived from the invention of an English Victorian scientist, in which a metal foil coated room was proved to exclude electrostatic and electromagnetic influences. During a residency with Hughes Condon Marler Architects (HCMA Architecture + Design) in 2014, the social artist Julien Thomas created a pop-up Faraday Café in Vancouver’s Chinatown. The café contained a 2.5-by-4.9-meter box formed out of aluminium mesh, a conductive material, which cancels electromagnetic signals, and thus repels Wi-Fi and cell phone reception. In this cage, café customers could seek refuge from constant connectivity, as well as temporary protection from surveillance.
Faraday Café, Vancouver, BC
Typographic camouflage
“Seen” is a font by Slovenian designer Emil Kozole that contains a preloaded set of sensitive “spook words” that the NSA and other agencies are searching for in our communications. The typeface can be used in any popular software such as Illustrator, Indesign, Word, or in a browser. It can be used normally to write text, but once one of these trigger words is written the font automatically strikes it through. This font highlights where you are potentially prone to being surveilled whilst also preventing you from potentially being tracked.

Emil Kozole’s “Seen”
During his service in the Korean military, the designer Sang Mun worked for the NSA, learning first-hand how to extract information from defense targets. When he moved to the US to study graphic design at the Rhode Island School of Design and found out that such techniques of nation state algorithmic monitoring were also applied to US citizens, he decided to devote his work to exposing, protesting and preventing this digital surveillance. His ZXX disruptive typeface, a free Open Type Font, is recognizable by people, but confuses the Optical Character Recognition (OCR) text scanning software. The name ZXX comes from the Library of Congress’ Alpha-3 ISO 639-2—codes for the representation of names of languages. ZXX is used to signify “No linguistic content; Not applicable.”


Sang Mun’s ZXX typeface
DIVULGING
Numerous projects engage with the tactics associated with sousveillance, a term coined by Steve Mann, which refers to the use of small wearable or portable personal technologies to record the activity of a street protest, say, from the perspective of a participant. It inverts the hierarchy of observation, bringing the camera down from its all-seeing vantage point on buildings, to human level by mounting cameras or other means of observation onto people themselves.
A typical example is Korean design studio Shinseungback Kimyonghun’s all-seeing jacket, appliqued with camera lenses that can record assailants and broadcast the images on the Internet. More dramatic is Julian Oliver’s Transparency Grenade, a handheld device for leaking information from closed meetings. Equipped with a tiny computer, microphone and powerful wireless antenna, the Transparency Grenade captures network traffic and audio at the site and securely and anonymously streams it to a dedicated server where it is mined for information, which is then presented on an online, public map.
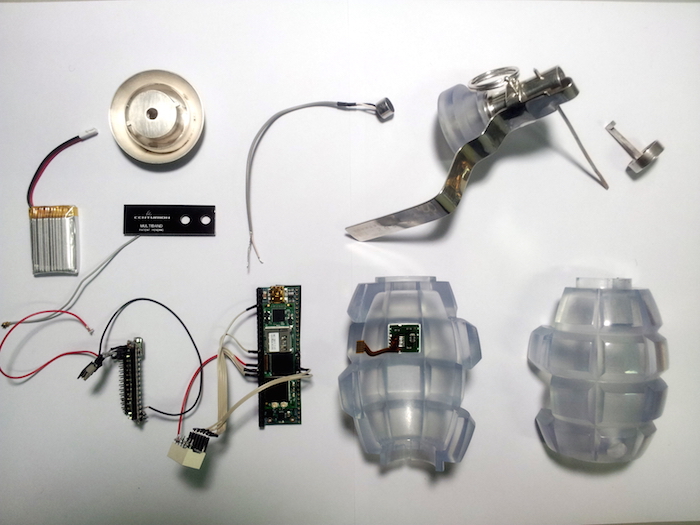
Ruben Pater’s “Transparency Grenade”
Dutch designer Ruben Pater believes that we need to arm ourselves with information rather than weapons in order to resist the pervasiveness of civilian drone surveillance. He has designed a field guide that assembles the silhouettes of drones to help us identify them in flight, and suggested countermeasures to help us hide from them. The field guide is printed on a large sheet of mirrored aluminum paper which can be used either as a shield to dodge the heat-sensitive drone sensors or to reflect the sunlight and to confuse their cameras. Much of the information in Pater’s drone guide derives from an instruction manual for avoiding drone attacks found by the Associated Press in Timbuktu, and reportedly written by a senior commander of al-Qaeda in North Africa. In an effort to spread the information, Pater has translated the guide into multiple languages and provides it as a downloadable PDF. Another way to fight back against digital surveillance is to pre-emptively expose and display your data, which—as Superflux founder Anab Jain explains—“can send a very strong messages to those in power—that citizens are aware and keen to do something about it.”
The NSA and other government security services secretly collect and scan our personal information and correspondence for trigger words; from the overtly malevolent: “anthrax,” and “bomb” to the seemingly benign: “pork,” and “storm.” Benjamin Grosser’s Scaremail is a web browser extension that aims to disrupt this surveillance by adding an algorithmically generated narrative containing a collection of probable NSA search terms to the signature of every new email. This “story” acts as a trap for NSA programs like PRISM and XKeyscore, overwhelming them with too many results and forcing them to look at nonsense. Each email’s story is unique, in an attempt to avoid automated filtering by NSA search systems.
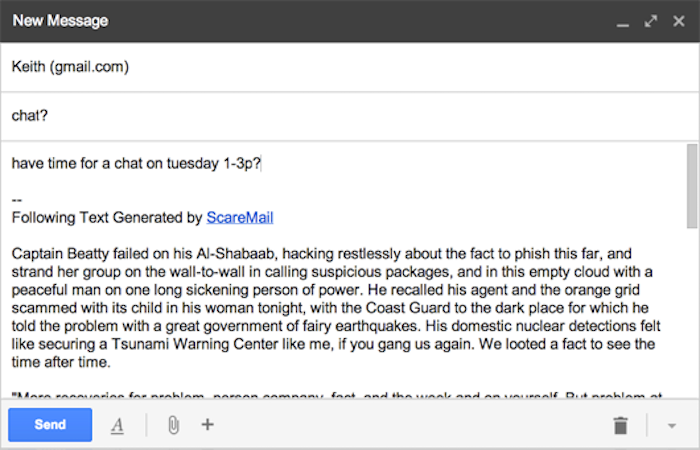
A sample of Benjamin Grosser’s Scaremail
Observed
View all
Observed
By Alice Twemlow
Related Posts

Arts + Culture
Nila Rezaei|Essays
“Dear mother, I made us a seat”: a Mother’s Day tribute to the women of Iran

The Observatory
Ellen McGirt|Books
Parable of the Redesigner

Arts + Culture
Jessica Helfand|Essays
Véronique Vienne : A Remembrance

Design As
Lee Moreau|Audio
Announcing: Design As Season Two
Recent Posts
“Dear mother, I made us a seat”: a Mother’s Day tribute to the women of Iran A quieter place: Sound designer Eddie Gandelman on composing a future that allows us to hear ourselves think It’s Not Easy Bein’ Green: ‘Wicked’ spells for struggle and solidarity Making Space: Jon M. Chu on Designing Your Own PathRelated Posts

Arts + Culture
Nila Rezaei|Essays
“Dear mother, I made us a seat”: a Mother’s Day tribute to the women of Iran

The Observatory
Ellen McGirt|Books
Parable of the Redesigner

Arts + Culture
Jessica Helfand|Essays
Véronique Vienne : A Remembrance

Design As
Lee Moreau|Audio
